A SIM is the short form for Subscriber Identity Module. This is a piece of plastic that slots into your mobile phone that acts as your unique ID so that you can connect to a mobile phone network. This allows you make calls and also send text messages. A SIM doesn’t have much memory as compared to a memory card, but it stores a lot of information needed to connect to a mobile phone network. This includes a unique ID called the IMSI (International Mobile Subscriber Identity) which is used to connect someone calling your mobile number to your phone, rather than to someone else’s. SIMs also store names and telephone numbers, which makes it much easier to switch phones without losing your contact details.
When did SIM cards first appear?
SIM cards first appeared with the digital ‘GSM’ mobile phones around 1992. Previously, there were analogue mobiles before the coming of SIM cards. Nokia 1011 was the first SIM card supported phone to go on market.
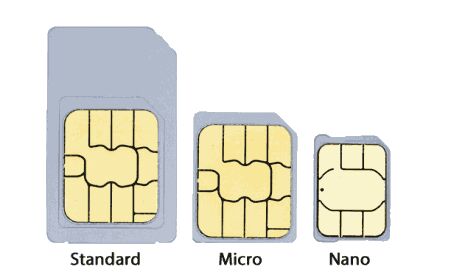
SIMs are getting smaller
The original Full-size SIM was fine for early digital mobile phones, but as mobile communications technology improved and the phones started to shrink, and so did the SIM card too. The first SIM card was the thumbnail-sized Standard-SIM. This was still provided as part of a full-size SIM for compatibility with older models, but it could be snapped out for use in newer phones. Standard-SIMs stuck around for many years, but once smartphones started to get smaller and thinner, space was in short supply. As a result the Micro-SIM standard was created in 2003, but manufacturers didn’t adopt it until 2010. The Micro-SIM was only a little smaller than the Standard-SIM and most of the missing size was useless plastic. That meant many Micro-SIMs could be cut down to size using widely available tools (or a steady hand and pair of scissors) without otherwise damaging them. Inevitably it wasn’t long before a still-smaller SIM was needed. In 2012 we got the Nano-SIM, which did away with all redundant plastic. It was essentially just a tiny chip. Most modern smartphones use a Micro or Nano SIM, but you can usually use a smaller SIM in a larger slot with an adapter.
SIM cards come with built-in security features to protect your account if your smartphone is stolen. First among these is a four-digit SIM PIN that, if enabled, must be entered whenever you restart your phone to ‘unlock’ it. Related Article: How to set up a SIM card lock on Android to secure your sensitive information Get this PIN wrong (you normally get three tries) and your SIM will be blocked. But you can unblock it with a call to your mobile operator. SIMs can also be blocked if you don’t pay your bill or if your phone is lost or stolen – but you will need to inform your mobile phone network of the loss or theft for that to happen. Some cellular phone carriers sell phones in a “locked” condition (either locked in with a particular service provider or a specific SIM). If you have such a cellular phone then you will not be able to use different SIM cards with it unless you can “unlock” your phone. If you have a country specific SIM card then it will most likely work only in the country of its origin. A Ugandan specific SIM card may give you limited coverage abroad, depending on the roaming agreements your provider has. Most country-specific SIM cards have voicemail so a caller can leave you a message if your cell phone is turned off or not reachable.
How does a SIM card work?
A SIM card has a small amount of memory and a very low-powered processor. The SIM card not only enables communication between the phone and its carrier, but stores information such as phone numbers, security data and more. Carriers of recent have begun using specialized SIM cards with so-called Secure Elements. A secure element is a tamper-resistant platform, typically a one chip secure microcontroller capable of securely hosting applications and their confidential and cryptographic data in accordance with the rules and security requirements set forth by a set of well-identified trusted authorities. While on the production line, certain information is written into the memory of a SIM card: the IMSI (International Mobile Subscriber Identity) in accordance to the carrier who ordered the batch, and a 128-bit key called Ki (Key Identification). Simply put, IMSI and Ki are the subscriber’s login and password respectively, hard-coded into the SIM card chip. The correspondence between a subscriber’s IMSI and the phone number is stored in a special database called HLR (Home Location Register). This data is copied into another database, VLR (Visitor Location Register) in each segment of the network, based on the subscriber’s temporary ‘guest’ registration to another base station. The authorization process is quite simple. When a subscriber is registered to the temporary database, VLR sends a random 128-bit number (RAND) to the phone number. The SIM card processor uses the A3 algorithm to generate a 32-bit response (SRES) to VLR, based on the RAND number and Ki. If VLR gets a matching response, the subscriber becomes registered in the network. Related Article: 5 Sim card management apps for Android SIM also generates another temporary key called Kc. Its value is calculated based on above mentioned RAND and Ki with the help of the A8 algorithm. That key, in turn, is used to encrypt transmitted data by means of the A5 algorithm. This might sound a bit complicated but the basic idea is simple: firstly you have a login and password hard-coded into the SIM, secondly you create verification and encryption keys with a couple of math tricks, and that’s it. The encryption is always enabled by default, however, in certain circumstances, for instance, provided a warrant, it is switched off, making it possible for an intelligence agency to intercept phone conversations. Back in the day, telephones used to have physical wires connecting one end to another. Whenever you dial a number your telephone company could row your call exactly where it needed to go using a cable. That has since changed with the emergence of SIM cards. Above is a brief guide on SIM cards. Key References used;
kaspersky.com